
SWARM
Traditionally penetration testing tools target hosts one at a time. SWARM differs in that it can deploy any CANVAS module, exploit or reconnaissance tool against large sections of a cyber range in minutes to hours.
SWARM is fast enough to run multiple times a day against even the biggest set of IPs. This allows for massive returns during your testing and modeling.
Traditionally penetration testing tools target hosts one at a time. SWARM differs in that it can deploy any CANVAS module, exploit or reconnaissance tool against large sections of a cyber range in minutes to hours.
download Swarm engagements PDF
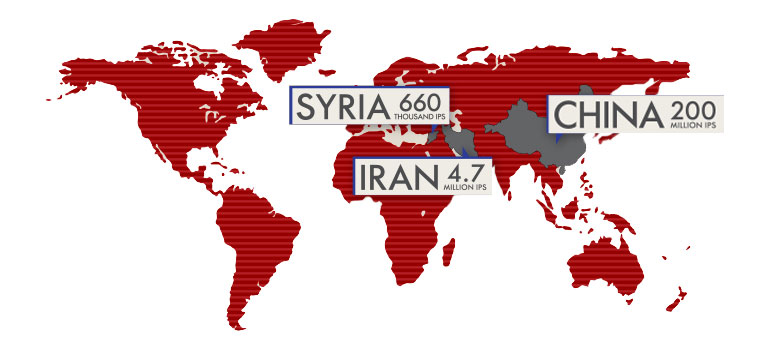 Speed
SpeedA default swarm can scan around a thousand IPs a minute, although this can be accelerated at additional cost for extremely time sensitive engagements.
The Immunity team will then look over the data SWARM has gathered, to provide potential avenues for an additional SWARM run, with perhaps a new security check, or a different configuration. The database created is extremely useful for follow-on engagements which focus on newly emerging threats.
Additionally, a common follow-on engagement is to run WebSiege to find SQL Injection vulnerabilities in every publicly accessible web application. Finally, a report is produced that explains our results and indicates possible courses of action. Keep in mind that the time estimates given here can vary and depend on the behavior of your network.
SWARM includes a subscription to CANVAS Early Updates – which often has exploits not found elsewhere and which are typically first to market. For example, the exploit for Samba NDR heap overflow (CVE-2012-1182, CVSS: 10) is included in SWARM, along with exploits for the Microsoft Padding Oracle (CVE-2010-3332, CVSS: 5.0) vulnerability.