
Davory undeletes files and recovers files from logically corrupted or formatted drives. Incorporates some of the data recovery techniques from WinHex and concentrates on ease of use. Offers two separate, fully automated data recovery mechanisms to maximize your chances of success. One mechanism works with files of any type, the other one recovers JPG, PNG, GIF, TIFF, BMP, MS Word/Excel/PowerPoint (DOC/XLS/PPS/...), RTF, MS Access (MDB), PostScript (EPS), Acrobat (PDF), Quicken (QDF), HTML, XML, DBX, PST, CAD (DWG), PSD, ZIP, GZ, RAR, RIFF (WAV, AVI), Real Audio/Media (RA, RAM, RM), Quicktime (MOV), Windows Media (ASF) and MPEG (MPG). Specifically supports FAT12, FAT16, FAT32, and NTFS. Powerful, yet inexpensive. Personal licenses for non-commercial use are offered at a reduced price.
As Davory works not only on hard drives, floppy disks, CDs, and DVDs, but also on CompactFlash cards, SmartMedia cards, memory sticks etc., it may save your day in particular if you are the owner of a digital camera. Davory can extract files of certain types (like JPEG or MS Office) or files matching certain filename patterns (like Invoice*.doc) conveniently and quickly with only a few mouse clicks. Other available languages: ![]()
![]() . Please try before you buy. The evaluation version will tell you if it can find your files and will recover files up to 200 KB. Please note that Davory is not guaranteed to successfully recover your files, depending on how serious your data loss scenario is. Davory cannot repair corrupt files.
. Please try before you buy. The evaluation version will tell you if it can find your files and will recover files up to 200 KB. Please note that Davory is not guaranteed to successfully recover your files, depending on how serious your data loss scenario is. Davory cannot repair corrupt files.
|
Davory can be run directly from a floppy disk or CD. It must not be installed on the same drive that contained the files you lost, as this might overwrite them. Such a drive must not be used any more principally, except for pure read operations. Writing to that drive (or just booting Windows from it) considerably diminishes chances of recovery. |
Davory does not recover the files it finds in place. It saves them to a different drive. That way the drive where the loss of data occurred will not be written to. It will not be altered at all, which is crucial for an uncompromised evidentiary procedure and guarantees that the data loss situation will not become even worse. |
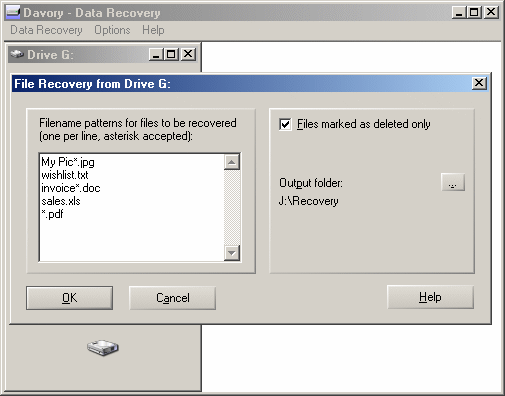
Limitations: